Secure by Design: Dynamic Watermarking for Enterprise Documents in C# .NET
Contracts, NDAs, audit reports, invoices, and HR exports are created on demand and downloaded as PDFs. Once a document leaves your application, traditional access control is lost. Dynamic watermarking adds a layer of security to your documents, making them traceable and less likely to be shared without authorization.
Enterprise applications generate documents dynamically. These include contracts, NDAs, audit reports, invoices, and HR exports, which are created on demand and downloaded as PDFs. Once a document leaves your application, traditional access control is lost. It can then be forwarded, archived, printed, or shared outside the original workflow.
This is why enterprise-grade document delivery relies on a layered approach. A single "CONFIDENTIAL" overlay is insufficient. You need documents to carry context about who downloaded them and when. You need machine-readable provenance for automated systems. You need forensic evidence that survives downstream workflows. You need tamper-evidence so the watermark cannot be removed without detection.
One practical solution is a four-part stamp.
First, add a visible stamp that communicates accountability to humans. Second, add metadata that systems can quickly read. Third, embed the same data in an attached JSON file to allow for greater forensic analysis and interoperability. Finally, digitally sign the resulting PDF so that any removal or modification of these elements is detectable.
The following sample shows exactly how to implement this pattern with TX Text Control for dynamically created documents.
The Four-Step Stamp Pattern
- Add a visual stamp
A visual stamp is a human-facing watermark. It discourages casual forwarding and preserves context when the file is viewed or printed. For dynamic documents, the stamp usually includes the recipient's name and email address, a timestamp, a document ID, and a fingerprint. - Add metadata
PDF metadata acts as a lightweight, machine-readable watermark. It can be indexed by document management systems (DMS), searched by compliance tools, and used in automated workflows without parsing page content. Metadata also survives common handling operations, such as emailing or archiving. - Attach the stamp data
Attaching the stamp payload as JSON provides a forensic and integration-friendly layer. It preserves the watermark semantics even when the document is converted to an image, printed, or routed through systems that do not reliably preserve metadata. It also provides a clear contract for downstream systems because the stamp is structured data, not just text. - Digitally sign the document
A signature acts as a guardrail. Without a signature, watermarks are editable. Once signed, any attempt to remove the visible stamp, change the metadata, or replace the attachment will invalidate the signature. This makes watermarking tamper-evident, which is what enterprises need when documents are used as evidence.
Sample: Stamping and Signing a Dynamic PDF with TX Text Control
The code below reflects the exact order of operations in production. First, you generate the stamp payload. Then, you apply the visual stamp to the document and embed the structured stamp data. Next, you set the PDF metadata. Finally, you sign the PDF at export time.
Build the Stamp Payload and Generate a Visual Stamp
The stamp payload serves as the single source of truth. Everything you embed later is derived from this object. In real systems, you populate these fields with information from the authenticated user, the request context, the tenant information, the document IDs, and the audit trail.
using System.Security.Cryptography.X509Certificates;
using System.Text;
using TXTextControl;
// 1) Build stamp payload + SVG
var stampSvg = new StampSvg();
var data = new StampSvg.StampData
{
RecipientName = "Tim Typer",
RecipientEmail = "tim.typer@example.com",
RecipientId = "E-10482",
DocumentTitle = "Master Services Agreement",
DocumentId = "MSA-2026-00219",
Reference = "CRM-88914",
IssuedAtUtc = DateTime.UtcNow,
IssuedBy = "Document Service",
Environment = "PROD",
Classification = "CONFIDENTIAL",
PolicyHint = "Personal copy. Redistribution prohibited.",
Fingerprint = Guid.NewGuid().ToString("D").ToUpperInvariant()
};
var svg = stampSvg.GenerateSvg(data);
var svgBytes = Encoding.ASCII.GetBytes(svg);
const int HeaderImageZOrder = 1;
const int MarginOffsetTwips = 200;
const int StampScalePercent = 60;In this example, we will create a simple payload containing a username, email address, timestamp, document ID, and random fingerprint. The visual stamp is generated by converting this data into an image. For production, use a more sophisticated design that incorporates your branding and security requirements.
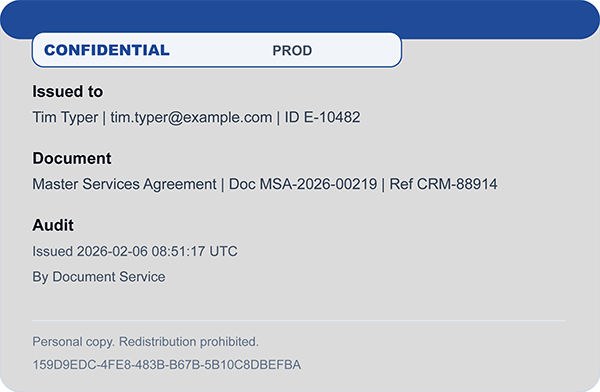
The stamp content creates accountability. The timestamp links it to a particular download event. The fingerprint makes each export unique, even when the underlying document content is the same. This uniqueness is valuable for leak investigations and correlating files with audit logs.
Using SVG for the visual stamp is practical because it scales cleanly, remains sharp in print, and can be designed to include branding, classification labels, and compact provenance fields.
Load the Template Document
This is where the "prepare now, finalize later" approach comes in. Your system can store either a clean template or a prepared document without user-specific information. When you download it, you can apply the stamp. This allows you to keep the template pristine and only add the watermark at the last moment, which is important for performance and security. This is an approach that should be valid for all PDF export processes.
// 2) Load document
using var tx = new TXTextControl.ServerTextControl();
tx.Create();
tx.Load("Sample_NDA.docx", TXTextControl.StreamType.WordprocessingML);
tx.PageUnit = MeasuringUnit.Twips;
// Cache section context (no behavior change)
var section = tx.Sections[1];
var headersAndFooters = section.HeadersAndFooters;
TXTextControl.HeaderFooter? GetOrCreateHeader()
{
var hdr = headersAndFooters.GetItem(TXTextControl.HeaderFooterType.Header);
if (hdr != null) return hdr;
if (headersAndFooters.Add(TXTextControl.HeaderFooterType.Header))
return headersAndFooters.GetItem(TXTextControl.HeaderFooterType.Header);
return null;
}You can keep templates reusable and avoid embedding personal data until it's required. This reduces risk, simplifies caching, and ensures that security and compliance rules are applied in the final export step.
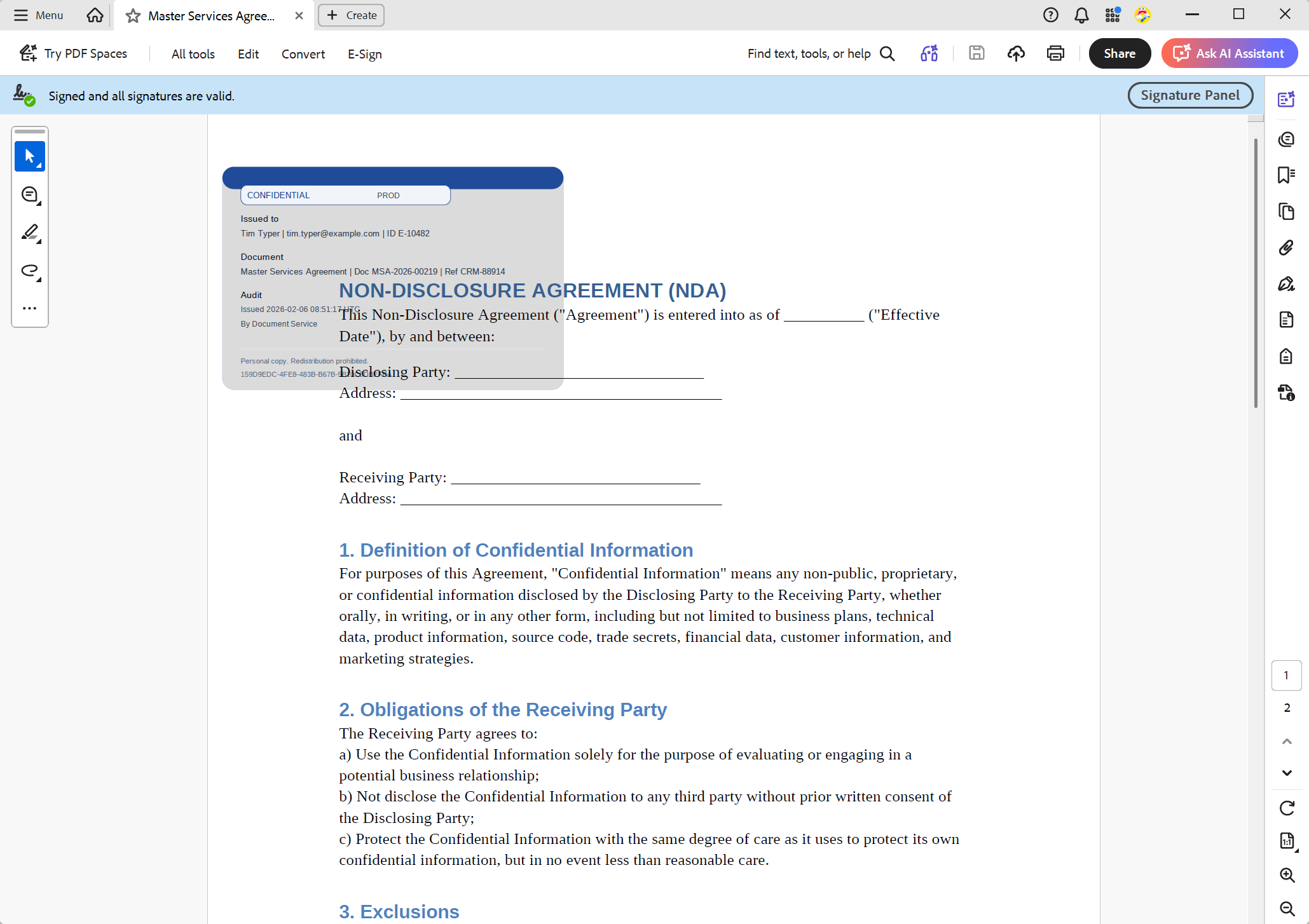
Add the Visual Stamp into the Header
The visible watermark should reliably appear on every page. It is commonly added to the header because it naturally repeats across pages and is less likely to be overlooked than a single stamp on the first page.
// 3) Add SVG stamp to header
var marginLeft = section.Format.PageMargins.Left - MarginOffsetTwips;
var header = GetOrCreateHeader();
if (header != null)
{
using (MemoryStream ms = new MemoryStream(
svgBytes,
0,
svgBytes.Length,
writable: false,
publiclyVisible: true))
{
TXTextControl.Image image = new TXTextControl.Image(ms);
header.Images.Add(
image,
HeaderImageZOrder,
new System.Drawing.Point((int)-marginLeft, 0),
TXTextControl.ImageInsertionMode.FixedOnPage |
TXTextControl.ImageInsertionMode.BelowTheText);
image.HorizontalScaling = StampScalePercent;
image.VerticalScaling = StampScalePercent;
}
}This is the deterrence layer. Even if a PDF is printed or screenshot, the user's identity and the time of download remain visible. With the "fixed on page" or "below the text" insertion modes, the stamp behaves like a true watermark rather than editable content that shifts with the text.
Embed the Stamp Payload as a JSON Attachment
This is the "invisible watermark with semantics." Instead of burying information only in rendered pixels, the full structured payload is attached. This allows downstream systems to easily extract the stamp data without parsing the visual content. This method also preserves the watermark semantics when the document is converted to an image, printed, or routed through systems that do not reliably preserve metadata.
// 4) Embed stamp data as JSON attachment
var json = System.Text.Json.JsonSerializer.Serialize(data);
tx.DocumentSettings.EmbeddedFiles = new[]
{
new TXTextControl.EmbeddedFile("stamp-data.json", json, null)
{
Description = "Stamp data in JSON format",
Relationship = "Alternative",
MIMEType = "application/json",
CreationDate = DateTime.Now,
}
};The following screenshot shows the attached JSON file in Adobe Acrobat. This attachment contains the same information as the visual stamp but in a structured format ideal for machine processing.
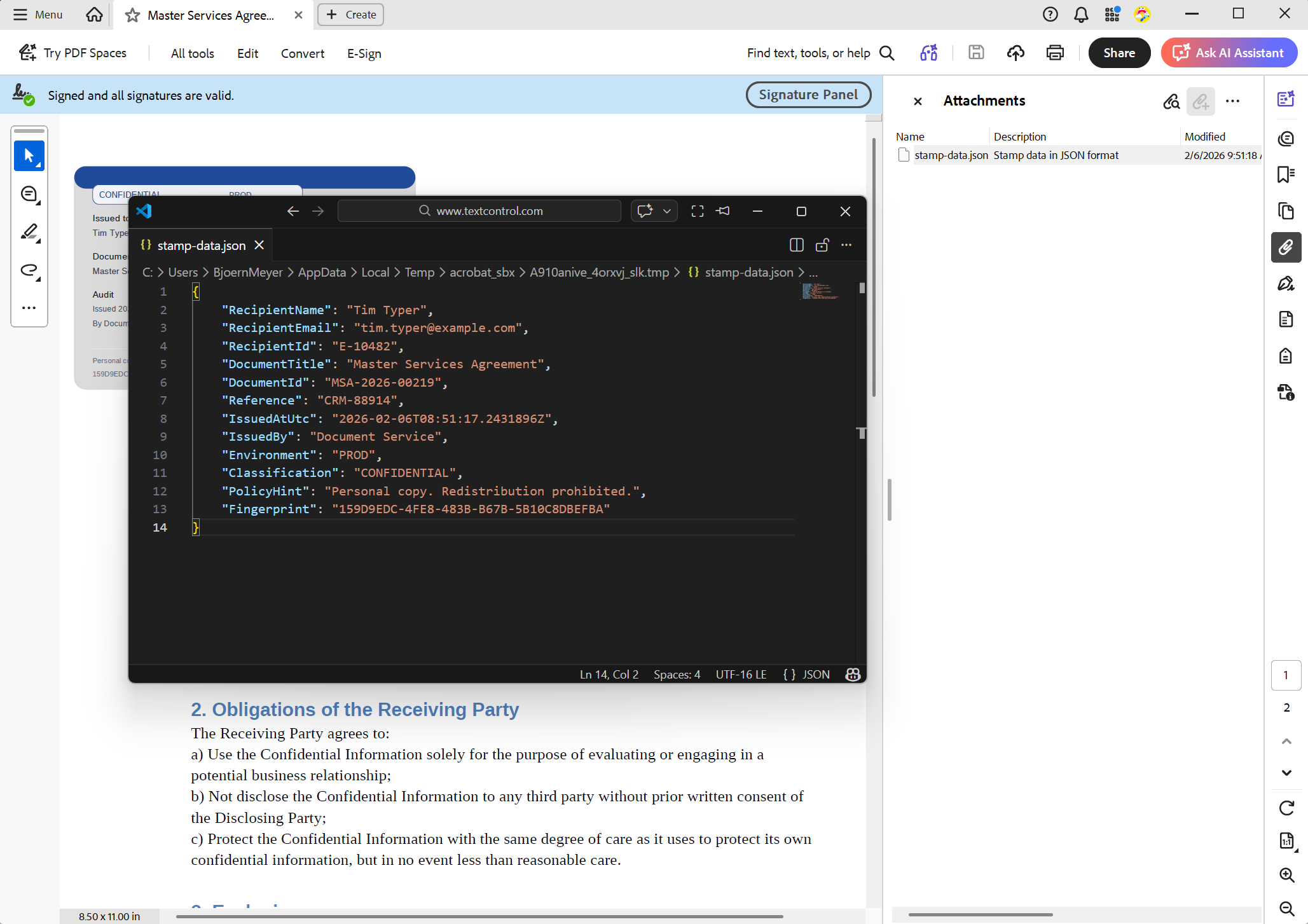
Attachments are useful for enterprise applications because they travel with the PDF. Downstream systems can extract them, archive them alongside the document, or inspect them during incident response. They also provide a robust forensic trail when metadata is stripped, normalized, or overwritten by third-party systems.
If you later need to confirm that a document corresponds to an audit entry, the JSON attachment offers a consistent payload that can be compared to your logs.
Add Metadata and Export as a Signed PDF
Finally, you can set the PDF metadata and digitally sign the output from the same stamp payload.
// 5) Load certificate + save as signed PDF + metadata
var certificate = X509CertificateLoader.LoadPkcs12FromFile(
"MyTXCert.pfx",
"123",
X509KeyStorageFlags.Exportable | X509KeyStorageFlags.MachineKeySet);
TXTextControl.SaveSettings saveSettings = new TXTextControl.SaveSettings()
{
Author = data.IssuedBy,
CreatorApplication = data.IssuedBy,
CreationDate = data.IssuedAtUtc,
DocumentKeywords = new[] { data.Classification, data.Environment, data.PolicyHint }
.Where(s => !string.IsNullOrEmpty(s))
.ToArray(),
DocumentSubject = data.DocumentId,
DocumentTitle = data.DocumentTitle,
LastModificationDate = DateTime.Now,
DigitalSignature = new DigitalSignature(certificate, null)
};
tx.Save("Stamped_NDA.pdf", TXTextControl.StreamType.AdobePDF, saveSettings);Metadata provides a fast path for enterprise systems. Indexers, document management systems (DMS) platforms, eDiscovery tools, and compliance scanners can read titles, subjects, keywords, authors, and timestamps without parsing page content or extracting attachments.
A digital signature makes the entire stamp trustworthy. Without a signature, someone could open the PDF in an editor, remove the header watermark, modify the metadata, delete the attachment, and redistribute an untraceable version. With a signature, however, those changes invalidate the signature, turning tampering into a detectable event. This is the difference between "we stamped it" and "we can prove it was not altered."
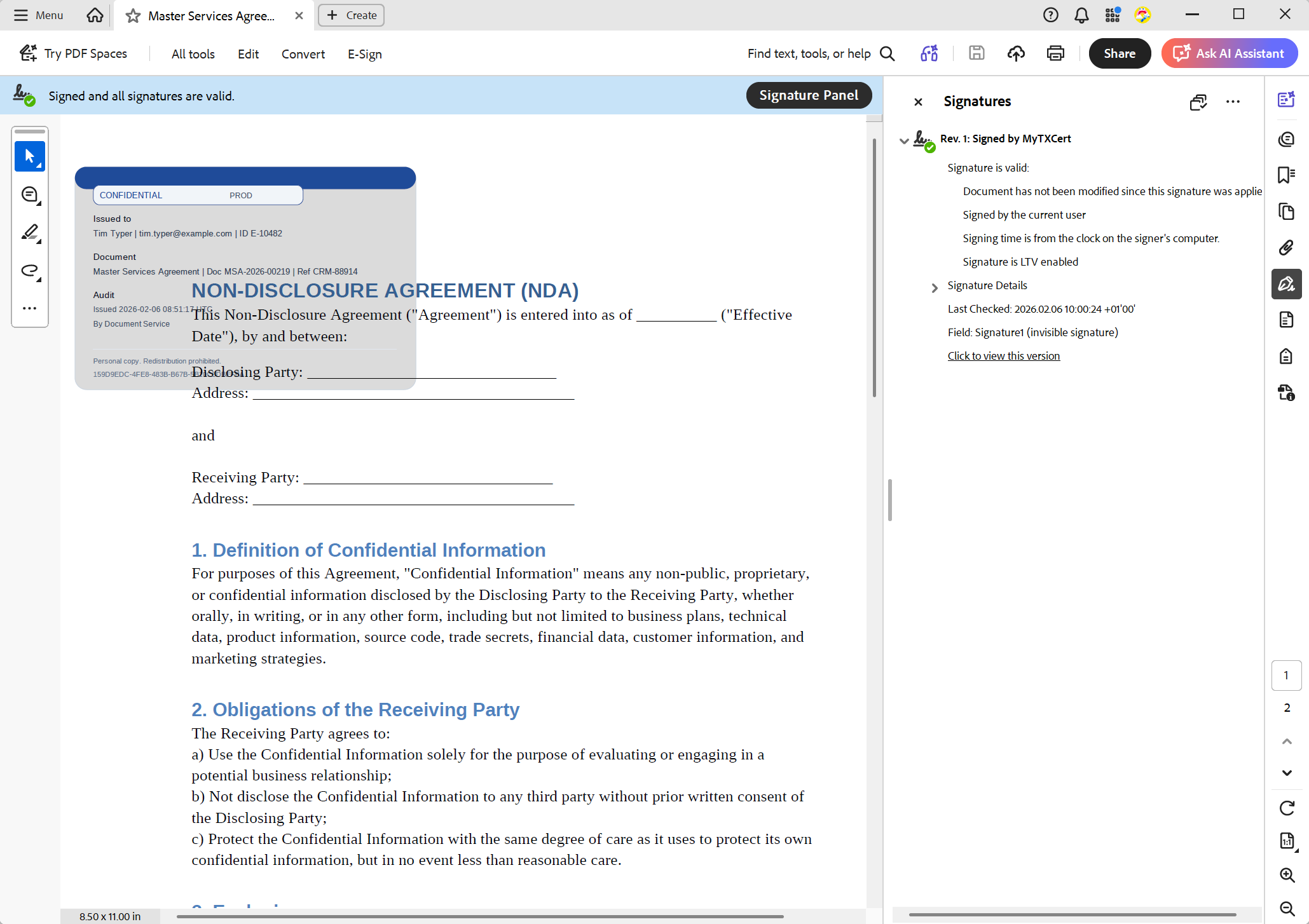
How This Looks in an Enterprise Workflow
In a typical enterprise application, templates and prepared documents are stored without personal watermarks. When a user downloads a document, the backend assembles the stamp payload using the user's identity and the context of the request. Then, it applies the visible stamp, embeds the metadata and JSON attachment, exports the document as a PDF, signs the result, and returns it to the client.
This process creates a unique, tamper-evident artifact for each download. If the document is leaked, the visible stamp provides immediate attribution. If the file is routed through automated systems, the metadata enables discovery and filtering. If a deeper investigation is needed, the attached JSON provides a structured forensic record. If someone tries to remove any of these elements, the signature alerts you.
This combination explains why this pattern is used in legal tech, financial services, healthcare portals, and internal reporting platforms. It scales well, is automatable, and respects the reality that documents will leave your system.
In summary, the four-step stamp pattern-visual watermark, metadata, attached JSON, and digital signature-provides a robust framework for securing dynamic documents in enterprise applications. This framework balances deterrence, machine-readability, forensic value, and tamper-evidence, meeting the complex needs of modern document workflows.
To learn how to implement this pattern in your application, check out the sample code and documentation for TX Text Control's PDF export and digital signature features.
![]()
Download and Fork This Sample on GitHub
We proudly host our sample code on github.com/TextControl.
Please fork and contribute.
Requirements for this sample
- TX Text Control .NET Server 34.0
- Visual Studio 2026
ASP.NET
Integrate document processing into your applications to create documents such as PDFs and MS Word documents, including client-side document editing, viewing, and electronic signatures.
- Angular
- Blazor
- React
- JavaScript
- ASP.NET MVC, ASP.NET Core, and WebForms
Related Posts
ASP.NETASP.NET CoreCertificate
How to Sign PDF Documents with PFX Certificates in .NET C# on Linux
This article shows how to sign PDF documents with PFX certificates in .NET C# on Linux. The sample code uses the TX Text Control .NET Server component to create a PDF document and digitally sign…
Adding Watermarks to PDF Documents in .NET C#
This article shows how to add watermarks to PDF documents using TX Text Control .NET Server. It discusses how to use SVG images as watermarks and how to position them in the document.
ASP.NETASP.NET CoreCertificate
How to Sign Signature Fields with Custom Signer Information and Time Stamps…
This article shows how to sign signature fields in a PDF document with custom signer information and timestamps using the TX Text Control .NET Server component in ASP.NET Core C#. The signature is…
ASP.NETASP.NET CoreData Protection
A Rule-Based PHI and PII Risk Scanner for Documents Using C# .NET
In this article, we explore how to implement rule-based text analysis in C# .NET to detect Protected Health Information (PHI) and Personally Identifiable Information (PII) within documents. We…
NDC London 2026 Wrap-Up: Conversations, Community, and a Conference Done Right
NDC London 2026 was an incredible experience filled with insightful conversations, a strong sense of community, and a well-organized conference that catered to developers' needs. Here's a wrap-up…






