Ransomware has many names: CryptoLocker, CryptoDefense or CryptoWall. These malware applications encrypt files on a PC and a complete network including network storage to extort money to unlock these files.
Ransomware is one of the most damaging threats companies face today. The malicious code is commonly spread through e-mail or compromised web sites, but also through USB flash drives.
A new trend in ransomware attacks is targeting hospitals and other healthcare facilities. Hospitals are collecting sensitive patient data and rely on accurate information from these records. Without quick access to this medical data in EHR and EMR systems, decisions and diagnoses are delayed and might result in halted patient care with fatal consequences. There are recent reports stating that paying the ransom is the quickest and most efficient way to restore the data. This is a very alarming trend. To cause damage, it is not always required to lock a complete network. Ransomware is able to detect the files and file servers with most traffic. In order to block the whole network, maybe 1 or 2 file servers need to be locked.
In March 2016, MedStar Health, that operates 10 hospitals and more than 250 out-patient clinics in the Washington, DC area, got hit by a virus that contained ransomware. According to an article from Washington Post, employees explained that they saw pop-ups on their computers demanding a Bitcoin payment.
Typical security practices against ransomware are:
- Off-site backups
- Disable macros in document attachments
- Block attachments
- Install patches early
- Monitor outbound traffic
- Educate your users
All of the above practices might reduce the risk of getting infected, but there are better ways to protect sensitive data. The following animated diagram shows the infection spreading in a typical internal network when one machine has been compromised.
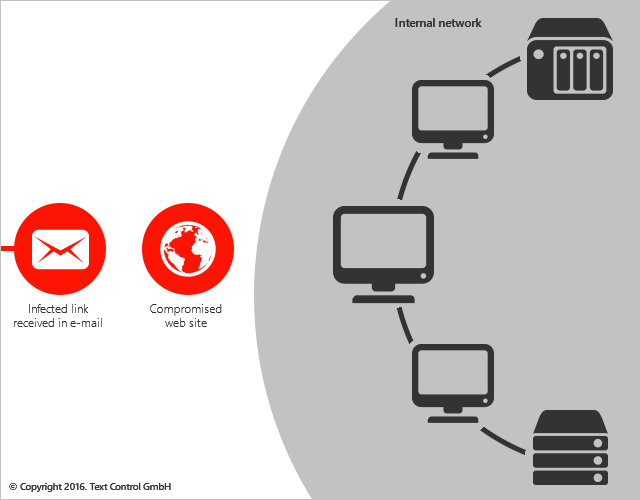
Solution: Disconnected Workstations
Text Control components drive leading EMR and EHR software packages. Text Control provides an MS Word inspired interface for cross-browser, cross-platform document editing and template creation. Mail merge and reporting processes can be directly integrated into EHR systems. Patient charting is done in a browser and documents and data are accessed using secure HTTP methods.
The following diagram shows workstations that are disconnected from the main network, databases and other critical elements:
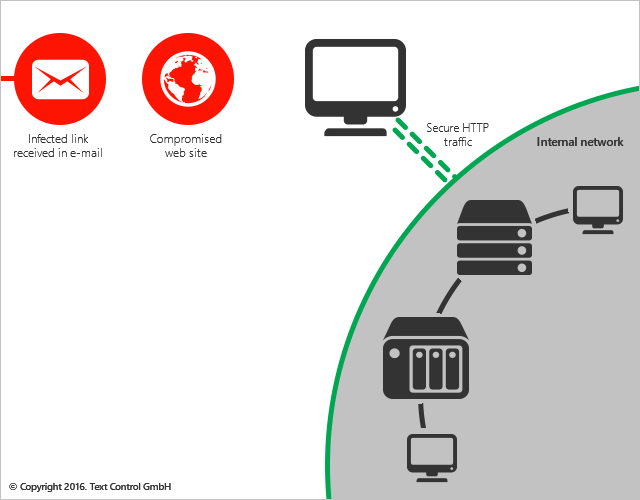
If the workstation gets encrypted, other machines and critical network elements are not affected.
The applications that use TX Text Control are not accessing local documents or data that is stored locally on workstations. Documents are loaded from web services using HTTP methods and can be directly modified in any browser. The workstation itself has no connection to the internal network or databases. The user of this isolated workstation has the same possibilities and options like on a connected workstation.
If you or your customers are facing these challenges, contact us to learn more about TX Text Control. As part of our consulting services, we can help with training and feasibility studies.






