Why Digitally Signing your PDFs is the Only Reliable Way to Prevent Tampering
PDF documents are widely used for sharing information because of their fixed layout and cross-platform compatibility. However, it is crucial to ensure the integrity and authenticity of these documents, especially when sensitive information is involved. Digitally signing PDFs is an effective way to prevent tampering and verify the document's source.

The PDF format is universal for business documents containing crucial information, including contracts, NDAs, reports, and invoices. However, this ubiquity poses a critical risk: a PDF can be altered without leaving a trace. Even minor modifications, such as changing a number, replacing a logo, or editing a date, can compromise a document's integrity.
Why PDF tampering is a real risk
A PDF is a structured file that can be opened, edited, and re-saved with various tools. Even if a file appears "locked," it can often be modified or annotated without detection. Text can be replaced, form fields can be changed, and entire pages can be swapped and the resulting document can still appear authentic.
Such tampering is invisible to the human eye, yet it can alter a document's meaning. This makes manual verification impossible and exposes businesses to serious legal and compliance risks.
How can you prove that a PDF has not been altered?
There are two main strategies:
- Storing a hash value externally (e.g., in a database).
- Digitally signing the PDF using a trusted certificate authority.
Although both methods can verify the integrity of a PDF, only digitally signing the document provides complete, portable, legally verifiable protection.
Option 1: Storing a hash value in a database
One simple approach to protecting the integrity of a PDF is to calculate a cryptographic hash (e.g., SHA-256) when the document is created and store the value in a secure database. Later, you can verify that the document has not changed by recalculating its hash and comparing the result to the stored value. We implemented this as a reference implementation in our Text Control eSign demo, which is available online. The full source code is available on GitHub.
See this live
To demonstrate a typical workflow and Text Control's electronic signature technology, we published a fully functional demo. With it, you can create and request signatures, sign documents, and validate executed PDF documents.
This method has several advantages.
- It is easy to implement and verify.
- It can be part of an internal audit trail.
- It detects changes as small as a single byte in the file.
Sample code: Calculating and storing a hash value
This sample illustrates an effective and straightforward integrity-check workflow that uses TX Text Control and a SHA-256 hash. First, a PDF is created and saved programmatically using TX Text Control. Then, a cryptographic hash of the generated file is stored, for example, in a database. When the document is retrieved later, the hash is recalculated and compared with the stored value. If the two values match, it is confirmed that the file has not been altered since its creation. This approach provides a lightweight method for detecting tampering when full digital signatures are not used.
using System;
using System.IO;
using System.Security.Cryptography;
using TXTextControl;
class Program
{
private const string OutputPath = "document.pdf";
static void Main()
{
try
{
var pdf = CreatePdf();
File.WriteAllBytes(OutputPath, pdf);
var originalHash = ComputeSha256(pdf);
var reloadedPdf = File.ReadAllBytes(OutputPath);
var reloadedHash = ComputeSha256(reloadedPdf);
var matches = CryptographicOperations.FixedTimeEquals(originalHash, reloadedHash);
Console.WriteLine($"Original Hash: {Convert.ToHexString(originalHash)}");
Console.WriteLine($"Reloaded Hash: {Convert.ToHexString(reloadedHash)}");
Console.WriteLine($"Document hash match: {matches}");
}
catch (Exception ex)
{
Console.Error.WriteLine(ex);
Environment.ExitCode = 1;
}
}
private static byte[] CreatePdf()
{
using var tx = new ServerTextControl();
tx.Create();
tx.Text = "This is a sample document. More text.";
tx.Save(out var bytes, BinaryStreamType.AdobePDF);
return bytes;
}
private static byte[] ComputeSha256(byte[] data) => SHA256.HashData(data);
}The output of this console application is as follows:
Original Hash: A604933D62BE66888928F1F5819F43BCDF1177F17753592C98BB74A8A251994A
Reloaded Hash: A604933D62BE66888928F1F5819F43BCDF1177F17753592C98BB74A8A251994A
Document hash match: TrueHowever, this approach has significant limitations. Verification relies entirely on access to the original database. Once the document is sent out of your system, for example when it is emailed or uploaded externally, you will no longer be able to verify it. This approach also does not provide proof of authorship. While you can detect modifications, you cannot determine who created or changed the document. Additionally, the verification method is not standardized, so it cannot be validated in standard PDF viewers or by third parties. This means that external trust and interoperability are not possible.
It is a reliable and safe method as long as you control the environment in which the PDF is stored. For example, it can be used in an invoice portal where customers can access and read their invoices.
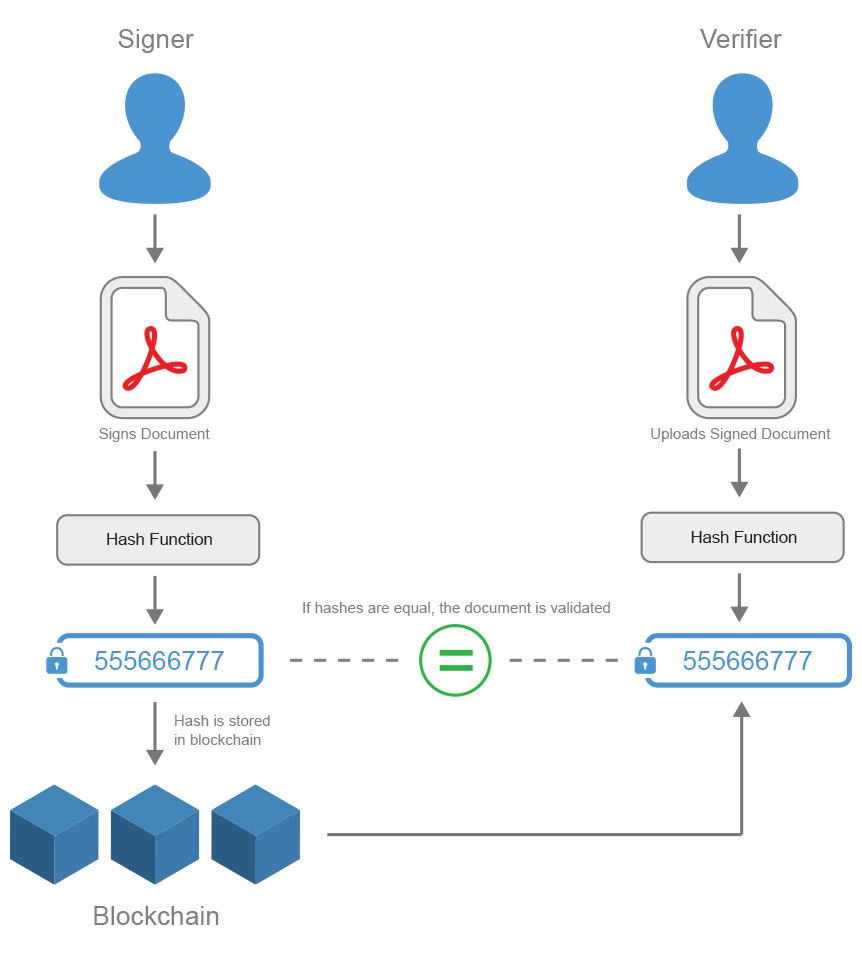
Storing documents on the blockchain
Another variation of this approach involves storing the hash value on a blockchain. This provides a decentralized, tamper-evident record of the document's integrity. However, like database storage, it does not prove authorship, and verification requires access to the blockchain. Furthermore, the use of blockchain technology can introduce unnecessary complexity and costs for some use cases.
Option 2: Digitally signing the PDF
To ensure PDF integrity, the most robust and legally verifiable method is to digitally sign the document using a trusted certificate authority (CA). Digital signatures use public key cryptography to generate a unique signature based on the document's content and the signer's private key. Any change to the document invalidates the signature, which provides strong evidence of its integrity.
When a PDF is signed:
- A hash of the document's content is created.
- This hash is encrypted with the signer's private key to create the digital signature.
- The digital signature, along with the signer's public key and certificate, is embedded in the PDF.
- A PDF viewer or a verification tool can later decrypt the signature using the public key, recalculate the document's hash, and compare it to the decrypted hash to verify integrity.
If even one character is changed, the hashes will differ and the viewer will immediately show that the file has been modified. Because the signature employs public-key cryptography (RSA or ECDSA) and a trusted certificate, it verifies both the document's integrity and the author's identity. This verification is portable; anyone can open the file in Acrobat or the TX Text Control verification tool to confirm its authenticity, and no external database is required.
Sample code: Digitally signing a PDF
The following sample code shows how to digitally sign a PDF document with TX Text Control. It creates a PDF, applies a digital signature with a certificate, and saves the signed document. This ensures that any subsequent changes to the document will invalidate the signature, providing strong integrity protection.
using System.Security.Cryptography.X509Certificates;
using TXTextControl;
// Define the certificate password and path
const string password = "123";
const string certificatePath = "certificate.pfx";
var cert = new X509Certificate2(certificatePath, password, X509KeyStorageFlags.Exportable);
// Initialize TXTextControl to create and save a document with the digital signature
using (var tx = new ServerTextControl())
{
tx.Create();
tx.Text = "Hello, World!";
// Prepare the digital signature for the document
var saveSettings = new SaveSettings
{
DigitalSignature = new DigitalSignature(cert, null)
};
// Save the document as a PDF with the digital signature
tx.Save("result.pdf", StreamType.AdobePDF, saveSettings);
}The role of certificates and trust
Every digital signature is based on a certificate issued by a trusted certificate authority (CA). The certificate verifies the signer's identity, ensuring that only authorized individuals or organizations can apply a trusted signature.
The signature process uses asymmetric encryption (RSA or ECDSA) and SHA-256 or stronger hashing algorithms. These standards are defined in ETSI EN 319 142-1 and ISO 32000-2, ensuring their interoperability and global recognition.
Why passwords and permissions are not enough
Password-protected or restricted PDFs only control who can open or edit a document; they don't verify that the document hasn't been altered. These protections vanish once the password is known or the file is exported. Therefore, they do not provide the same level of integrity assurance as digital signatures.
However, a digital signature travels with the document. It can be verified anywhere, at any time, without requiring a specific system or software configuration.
Why digital signatures are the only complete solution
In summary, storing a hash value in a database can provide a limited level of integrity verification, but only in controlled environments. It lacks portability and legal recognition. In contrast, digitally signing a PDF provides a robust, portable, legally verifiable method to ensure document integrity and authenticity. For businesses handling critical documents, digital signatures are the only complete solution for protecting against PDF tampering.
| Criterion | Database Hash | Digital Signature |
|---|---|---|
| Detects Tampering | ✅ Yes | ✅ Yes |
| Proves Authorship | ❌ No | ✅ Yes |
| Works Outside Your System | ❌ No | ✅ Yes |
| Legally Binding | ❌ No | ✅ Yes |
| Portable Verification | ❌ No | ✅ Yes |
A digital signature transforms the PDF into a self-verifying container. The file's cryptographic integrity and the signer's identity travel with it, ensuring that verification does not depend on any external system, database, or proprietary process.
How TX Text Control secures and elevates your PDF workflows
TX Text Control offers complete support for creating, signing, and verifying digitally signed PDFs. With built-in methods for applying digital signatures using trusted certificates, TX Text Control ensures your PDF documents' integrity and authenticity throughout their lifecycle. Whether you're generating contracts, invoices, or reports, TX Text Control's digital signature capabilities help protect your critical business documents from unauthorized alterations.
Rather than treating PDFs as static files, TX Text Control transforms them into reliable, verifiable digital records designed for the long term.
Rather than treating PDFs as static files, TX Text Control transforms them into reliable, verifiable digital records designed for the long term. This platform has native support for X.509 certificate-based digital signatures at its core. Developers can apply invisible cryptographic signatures to protect the integrity of data or visible signatures to facilitate end-user workflows. Certificates issued by trusted certificate authorities can be used to prove authorship, detect tampering, and establish legal non-repudiation. Thanks to secure timestamps, multiple-signature workflows, and compatibility with qualified certificates under eIDAS, TX Text Control-generated PDFs are ready for regulated environments, cross-border trust systems, and high-assurance business processes.
TX Text Control goes beyond security to support documents that remain useful and compliant for decades. With its first-class PDF/UA support, documents are generated with proper tagging, structure, and semantic layers. This ensures accessibility for assistive technologies and guarantees that document content can be interpreted by humans, as well as by future AI systems and automated pipelines.
TX Text Control provides full generation capabilities for both PDF/A-3a and PDF/A-3b. This standard is essential for long-term archiving and maintaining audit-safe business records. It ensures visual fidelity, reliable reproduction, and preservation of original content, even decades into the future. With PDF/A-3, developers can embed structured data, such as XML, JSON, ZUGFeRD, Factur-X, or DOCX originals, as well as machine-readable sidecar files, directly inside a PDF.
Conclusion
Protecting the integrity of PDF documents is crucial. Although storing a hash value in a database provides a basic level of tamper detection, this method lacks portability, authorship verification, and legal recognition. Digital signatures offer a comprehensive solution that ensures the integrity and authenticity of PDF documents. Leveraging trusted certificates and robust cryptographic methods, digital signatures reliably safeguard critical business documents against unauthorized alterations. Organizations seeking to maintain the trustworthiness of their PDFs should implement digital signatures.
ASP.NET
Integrate document processing into your applications to create documents such as PDFs and MS Word documents, including client-side document editing, viewing, and electronic signatures.
- Angular
- Blazor
- React
- JavaScript
- ASP.NET MVC, ASP.NET Core, and WebForms
Related Posts
A Complete Guide to Converting Markdown to PDF in .NET C#
Learn how to convert Markdown to PDF in .NET C# using Text Control's ServerTextControl component. This guide covers setup, conversion process, and customization options for generating high-quality…
ASP.NETASP.NET CoreDocument Creation
Why PDF Creation Belongs at the End of the Business Process
This article discusses why placing PDF creation at the end of the business process is important for ensuring accuracy and efficiency. The most scalable systems delay PDF generation until the…
Designing the Perfect PDF Form with TX Text Control in .NET C#
Learn how to create and design interactive PDF forms using TX Text Control in .NET C#. This guide covers essential features and best practices for effective form design.
Why Defining MIME Types for PDF/A Attachments Is Essential
The PDF/A standard was created to ensure the long-term reliable archiving of digital documents. An important aspect of the standard involves properly handling embedded files and attachments within…
Validate Digital Signatures and the Integrity of PDF Documents in C# .NET
Learn how to validate digital signatures and the integrity of PDF documents using the PDF Validation component from TX Text Control in C# .NET. Ensure the authenticity and compliance of your…






