Impact by "PrintNightmare" Vulnerability on DocumentEditor
Microsoft already released a patch for the vulnerability called "PrintNightmare" or CVE-2021-34527. This article explains the impact by the workarounds on the functioning of the TX Text Control online editor.

A critical security vulnerability (CVE-2021-34527) potentially allows to the installation of manipulated printer drivers in order to execute malicious code. Microsoft already patched this vulnerability for all Windows versions including Windows Server 2012, 2016 and Windows 10.
Print Spooler Usage: WYSIWYG
The online document editor Text
Offical Workarounds
Microsoft suggested two workarounds in case the patch cannot be applied:
- Disable the Print Spooler service
- Disable inbound remote printing through Group Policy
Impact of Workarounds
-
Disable the Print Spooler service
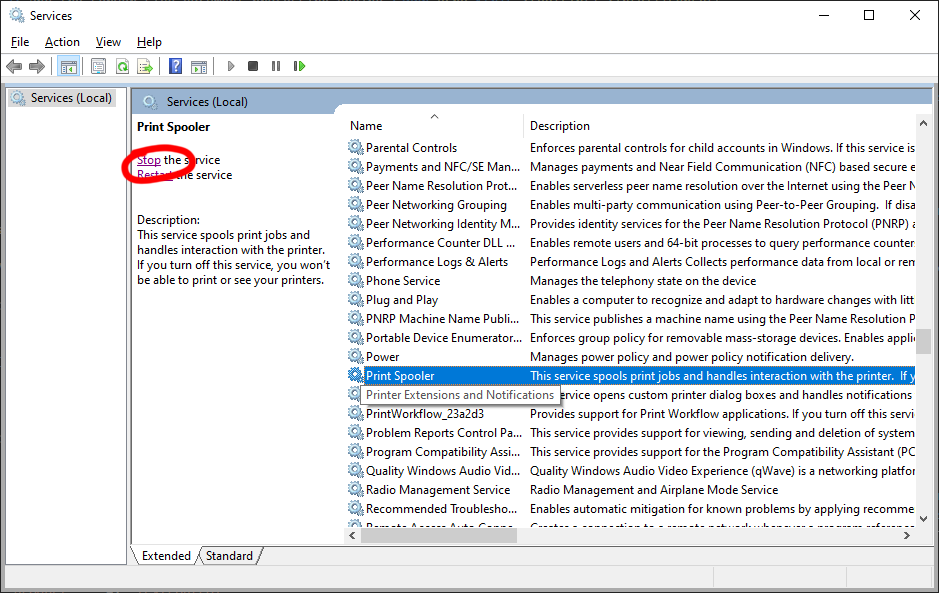
The first recommendation from Microsoft is to disable the Print Spooler completely. Disabling the Print Spooler service disables the ability to print both locally and remotely. By default, TX Text Control uses the default printer driver to render the text. If the printer driver is not available in case the Print Spooler is deactivated, the fallback solution for TX Text Control is the usage of the screen device. The fallback is selected automatically and no further action is required on your side. The rendering is then not based on a selected / or default printer driver, but uses the screen device. The rendering might differ from the normal view and documents might be rendered differently. But TX Text Control itself is fully functioning.
In case that you selected a specific printer to render the text by using the set
Formatting property, this printer is no longer used and the fallback comes into action.Printer In order to disable the Print Spooler, the "Print Spooler" service must be deactivated.
-
Disable inbound remote printing through Group Policy
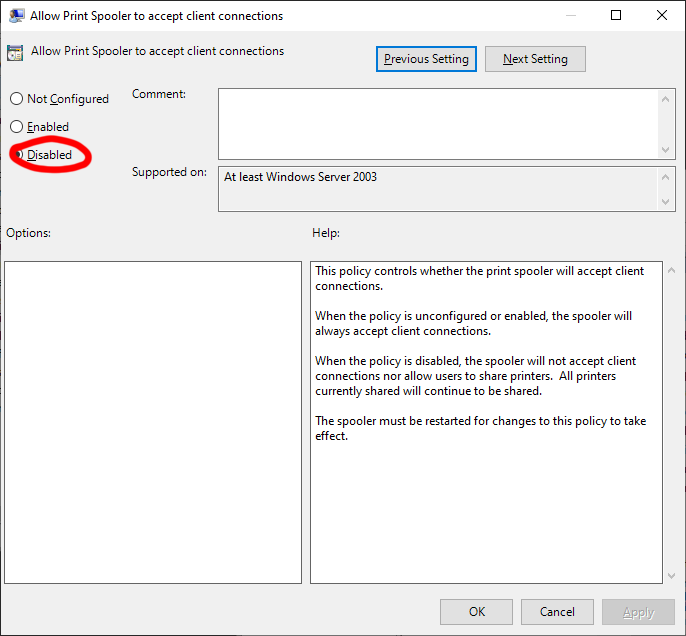
This policy will block the remote attack vector by preventing inbound remote printing operations.
Adding this workaround has no influence to the functioning of TX Text Control. In this case, TX Text Control is still able to the Print Spooler to render the text.
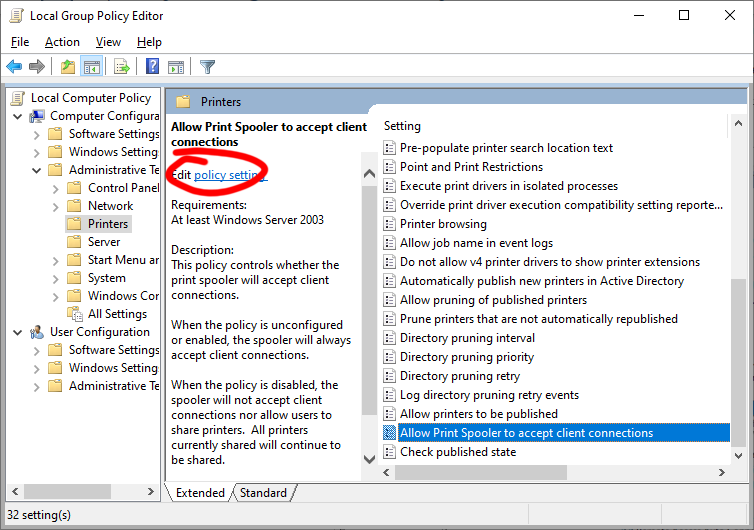
To enable this workaround, open the Group Policy, find the Computer Configuration / Administrative Templates / Printers entry, edit the policy setting and set the setting to Disable.
We highly recommend to apply the patch provided by Microsoft. Learn more about this here:
Windows Print Spooler Remote Code Execution Vulnerability
Microsoft is also recommending to check some registry entries to confirm the applied patch.
From Microsoft:
In addition to installing the updates, in order to secure your system, you must confirm that the following registry settings are set to 0 (zero) or are not defined (Note: These registry keys do not exist by default, and therefore are already at the secure setting.), also that your Group Policy setting are correct:
- HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows NT\Printers\PointAndPrint
- NoWarningNoElevationOnInstall = 0 (DWORD) or not defined (default setting)
- UpdatePromptSettings = 0 (DWORD) or not defined (default setting)
ASP.NET
Integrate document processing into your applications to create documents such as PDFs and MS Word documents, including client-side document editing, viewing, and electronic signatures.
- Angular
- Blazor
- React
- JavaScript
- ASP.NET MVC, ASP.NET Core, and WebForms






