PDF Security for C# Developers: Encryption and Permissions in .NET
In this article, we will explore how to implement PDF security in .NET applications using TX Text Control. We discuss encryption methods and permission settings that protect sensitive information in PDF documents.

When working with sensitive documents in digital workflows, securing the content is often just as important as creating it. TX Text Control provides developers with a robust set of tools to protect PDF files, including encryption and control over how the document can be used after opening. This article explores how encryption and permissions work together in PDFs and how TX Text Control can help you implement both in your .NET and web applications.
Understanding PDF Security: Encryption and Permissions
PDF security relies on two distinct mechanisms: Encryption and permissions. Although they are often mentioned together, they serve different purposes. Encryption protects documents by requiring a password to open them. Without the correct password, the content remains inaccessible. Permissions, on the other hand, determine what a user can do with the document after opening it. For example, you could allow a user to read a document but prevent them from printing or copying its contents.
Encryption: The First Line of Defense
Using TX Text Control, developers can apply both user and owner passwords to PDFs. A user password grants access to open the document. Without it, the file remains encrypted using robust AES algorithms. Once the document is opened, the owner password determines the viewer's level of interaction, whether they can edit the content, print it, extract text, or add annotations. These restrictions are part of the PDF specification and are supported by compliant PDF viewers.
However, it's important to understand the limitations of permissions. Unlike encryption, which is strictly enforced at the cryptographic level, permissions depend on the viewer's cooperation. Most professional-grade PDF readers, such as Adobe Acrobat, respect these flags. But others, especially open-source or less sophisticated tools, may ignore them entirely. Therefore, permissions should not be your only line of defense. Encryption should always be used when confidentiality is a priority.
Implementing PDF Security with TX Text Control
TX Text Control seamlessly implements this kind of security across platforms. Whether you're developing a Windows desktop application, a web-based solution with ASP.NET Core, or integrating PDF generation into a JavaScript-based front end, the APIs are designed to provide a consistent experience. With just a few lines of code, you can apply encryption and set permission flags, allowing developers to focus on the user experience without getting bogged down in low-level cryptography.
Best practice for securing a document is to set different values for the user and owner passwords. This ensures that even authorized viewers cannot change the document's permissions or remove its protection without knowing the owner password. Depending on the chosen configuration, TX Text Control uses encryption, which meets modern security standards for most business and legal use cases.
If a user password is used to encrypt a document, the user will be prompted to enter the password to open it. The SaveSettings are used to provide the password. The following code snippet shows how to set the password when saving a document as a PDF.
using (TXTextControl.ServerTextControl tx = new TXTextControl.ServerTextControl())
{
tx.Create();
TXTextControl.Selection selection = new TXTextControl.Selection();
selection.Text = "Hello PDF!";
selection.FontSize = 360;
selection.FontName = "Arial";
selection.ForeColor = System.Drawing.Color.Red;
tx.Selection = selection;
TXTextControl.SaveSettings saveSettings = new TXTextControl.SaveSettings()
{
UserPassword = "textcontrol"
};
tx.Save("output.pdf", TXTextControl.StreamType.AdobePDF, saveSettings);
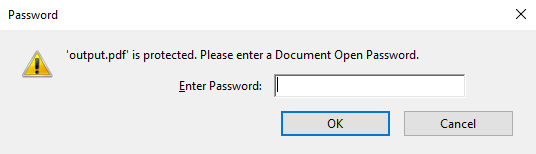
}When this document is opened in Acrobat Reader, the user is prompted for the password. The user must enter the password to open the document.
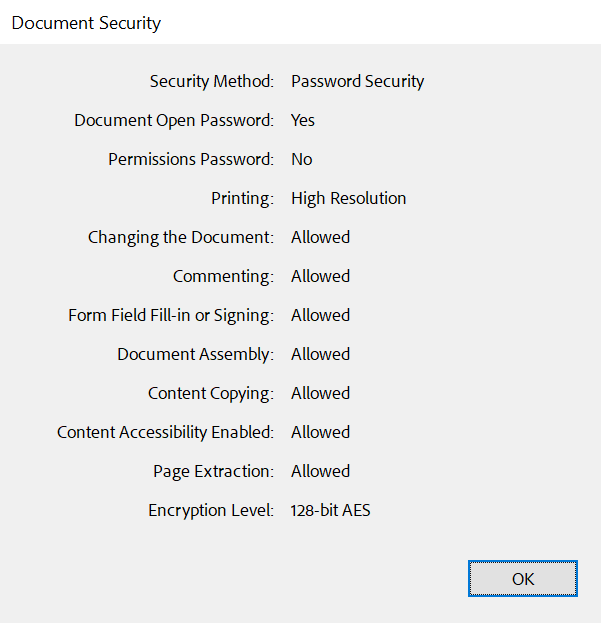
You can verify document security in Acrobat Reader using the document security settings. These documents will be encrypted and invisible to web search engines.
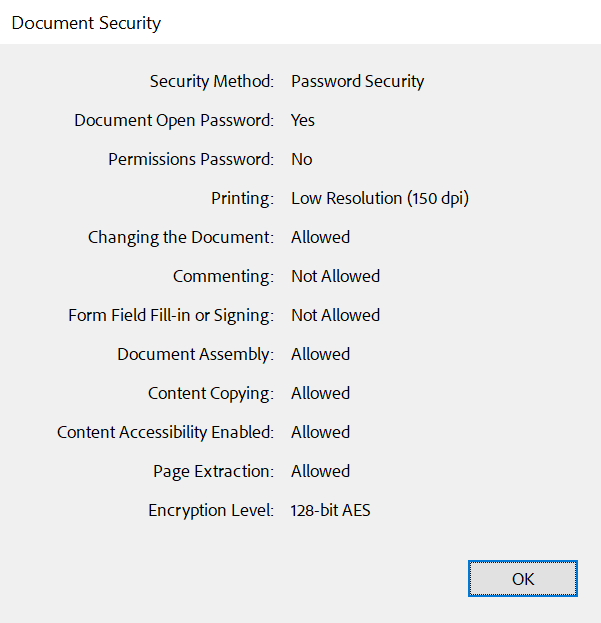
A variety of restrictions, such as printing, copying, and editing, can be set when the master password is specified.
For example, the following code snippet shows how to set the permissions when saving a document as a PDF.
using (TXTextControl.ServerTextControl tx = new TXTextControl.ServerTextControl())
{
tx.Create();
TXTextControl.Selection selection = new TXTextControl.Selection();
selection.Text = "Hello PDF!";
selection.FontSize = 360;
selection.FontName = "Arial";
selection.ForeColor = System.Drawing.Color.Red;
tx.Selection = selection;
TXTextControl.SaveSettings saveSettings = new TXTextControl.SaveSettings()
{
UserPassword = "textcontrol",
MasterPassword = "textcontrol",
DocumentAccessPermissions = TXTextControl.DocumentAccessPermissions.AllowGeneralEditing |
TXTextControl.DocumentAccessPermissions.AllowLowLevelPrinting |
TXTextControl.DocumentAccessPermissions.AllowExtractContents
};
tx.Save("output.pdf", TXTextControl.StreamType.AdobePDF, saveSettings);
}The security settings of the Adobe PDF document will be reflected by these settings.
These are the limits that TX Text Control can handle.
- AllowAll:
After the document has been opened, no further document access is restricted. - AllowAuthoring:
Allows comments to be added and interactive form fields (including signature fields) to be filled in. - AllowAuthoringFields:
Allows existing interactive form fields (including signature fields) to be filled in. - AllowContentAccessibility:
Allows content access for the visually impaired only. - AllowDocumentAssembly:
Allows the document to be assembled (insert, rotate or delete pages and create bookmarks or thumbnails). - AllowExtractContents:
Allows text and/or graphics to be extracted. - AllowGeneralEditing:
Allows the document contents to be modified. - AllowHighLevelPrinting:
Allows the document to be printed. - AllowLowLevelPrinting:
Allows the document to be printed (low-level).
Learn More
TX Text Control provides a sophisticated way to create and secure PDF documents, ensuring confidentiality and integrity. This article discusses the various options and safeguards for securing PDFs.
Conclusion: Encryption and Permissions in Harmony
With TX Text Control, you can integrate this multi-layered approach into your document processing pipelines without sacrificing performance or flexibility. You can create, secure, and deliver documents with precise control over who can open them and what they can do with them, ensuring both usability and protection within the same workflow.
In short, encryption and permissions work together to ensure a secure document experience. TX Text Control provides developers with the tools necessary to enforce access with strong encryption and guide usage through permissions. Although permissions alone are not foolproof, they provide an important additional layer of control when used responsibly alongside encryption. As always, the strongest security comes from thoughtfully implementing both technology and policy. Learn how to evaluate security features when selecting a PDF library in this comprehensive guide to choosing the right C# PDF generation library.
ASP.NET
Integrate document processing into your applications to create documents such as PDFs and MS Word documents, including client-side document editing, viewing, and electronic signatures.
- Angular
- Blazor
- React
- JavaScript
- ASP.NET MVC, ASP.NET Core, and WebForms
Related Posts
How to Verify PDF Encryption Programmatically in C# .NET
This article explains how to programmatically verify the encryption of a PDF document using C# .NET. It provides the necessary steps and code examples to ensure the PDF is encrypted correctly,…
A Complete Guide to Converting Markdown to PDF in .NET C#
Learn how to convert Markdown to PDF in .NET C# using Text Control's ServerTextControl component. This guide covers setup, conversion process, and customization options for generating high-quality…
ASP.NETASP.NET CoreDocument Creation
Why PDF Creation Belongs at the End of the Business Process
This article discusses why placing PDF creation at the end of the business process is important for ensuring accuracy and efficiency. The most scalable systems delay PDF generation until the…
Designing the Perfect PDF Form with TX Text Control in .NET C#
Learn how to create and design interactive PDF forms using TX Text Control in .NET C#. This guide covers essential features and best practices for effective form design.
Why Defining MIME Types for PDF/A Attachments Is Essential
The PDF/A standard was created to ensure the long-term reliable archiving of digital documents. An important aspect of the standard involves properly handling embedded files and attachments within…






